ServiceNow Integration
this blog is the third part of the tutorial.
Part 3: ServiceNow integration with PingFederate
Part 4: Office 365 integration with PingFederate
Part 5: PingFederate integration with Workspace ONE Access
Introduction
In this part of this PingFederate integration with Workspace ONE Access series, we’ll add our first service provider. I’m using ServiceNow as it’s rather popular and they offer developer tenants for free, but you can of course use any other SAML capable app in your own setup.
This tutorial will require following steps to be completed:
- Request a ServiceNow developer tenant
- Install ServiceNow Provisioner files on PingFederate
- Configure a MID server for LDAP integration
- Sync AD user objects to ServiceNow
- Configure SAML in ServiceNow
- Configure ServiceNow as a service provider in PingFederate
To complete the tasks in this chapter, you’ll need following components:
- service account in Active Directory that’s used to perform LDAP queries
Please note: I’m not a ServiceNow consultant, so don’t use this procedure in a production environment!
Request a ServiceNow developer tenant
First of all, you’ll need to request your free ServiceNow developer tenant on https://developer.servicenow.com/dev.do#!/home.
I opted to remove the demo data that’s automatically populated in the tenant to keep it nice and clean, but that’s up to you. Do note that the process takes some time to complete.
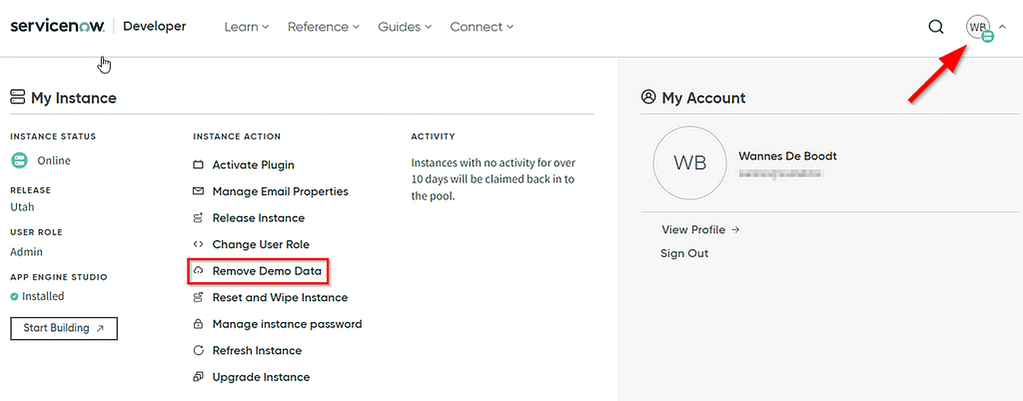
Configure a MID server
I’m installing the MID server software on the server that’s running my ACC and Workspace ONE Access connector roles. The ServiceNow documentation can be consulted here.
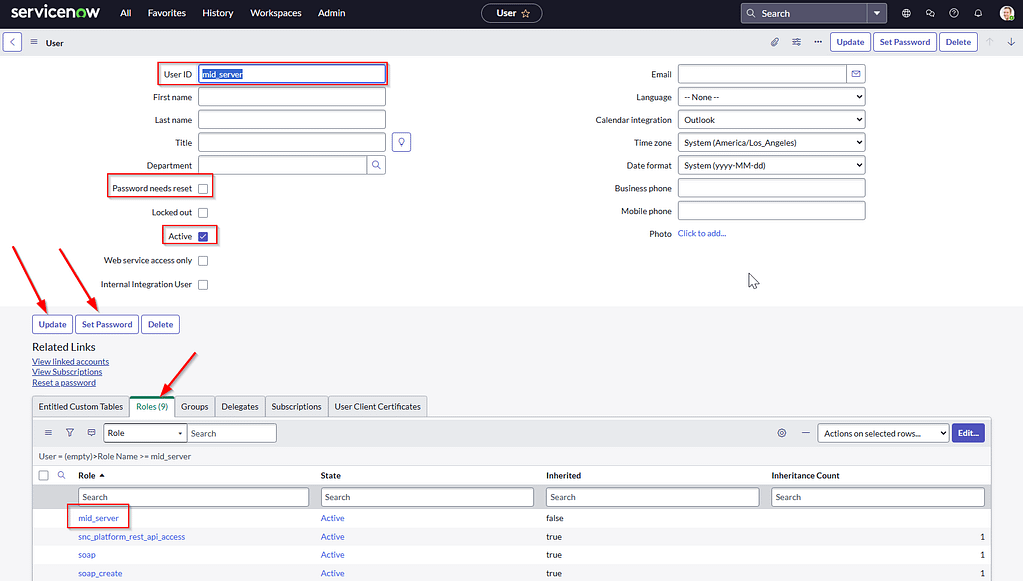
First, create a user account for the MID server software that allows the MID server to talk to ServiceNow. Set a password for the user and assign it the proper administrative role (mid_server). Don’t forget to press Update after each of these steps and make sure to unselect “Password needs reset”.
Next, download and run the installer:
NOTE: you’ll have to launch the installer from an elevated command prompt.
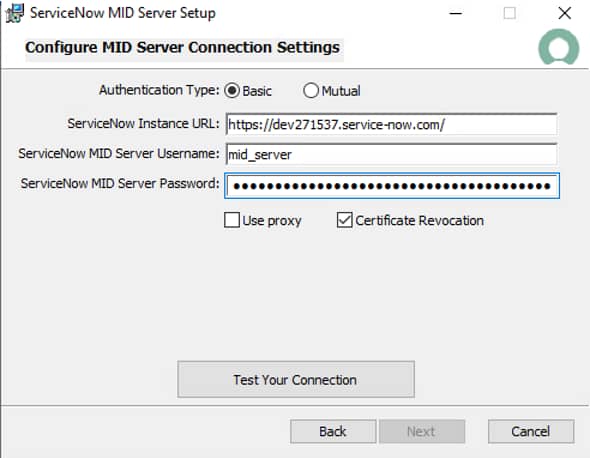
Provide your ServiceNow tenant URL and user credentials:
Next, to create a local account on the server, press the +sign and enter a username and password:

Press next till the software installs. In the ServiceNow console > Mid Server > Servers, you should now be able to see your machine. Open it and click the validate button leaving the default settings.
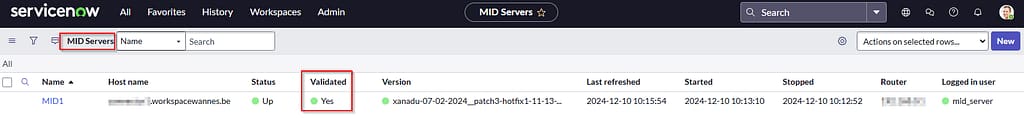
Sync AD user objects to ServiceNow
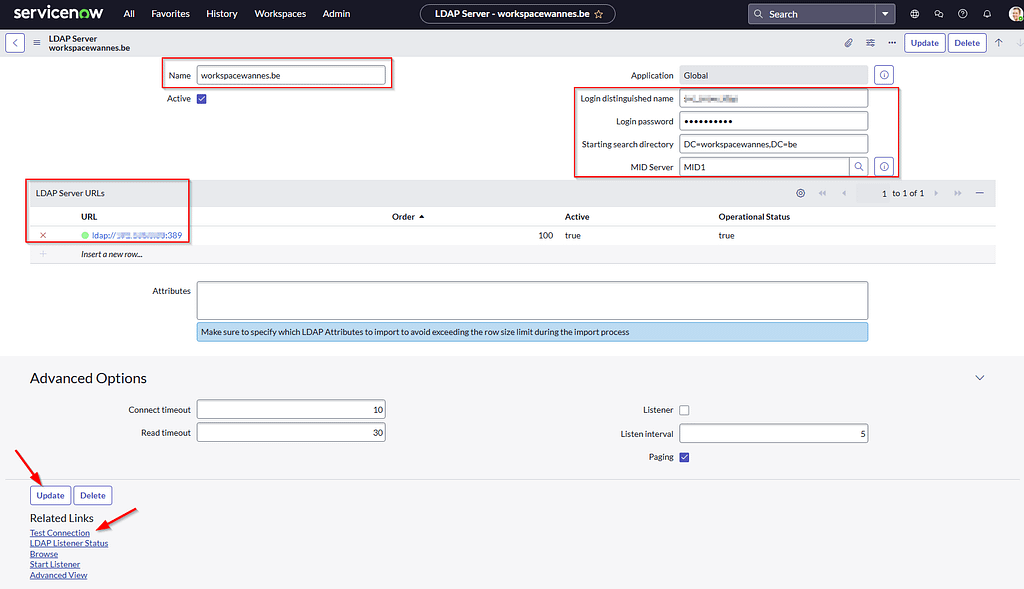
With the MID server installed and validated, we can create an LDAP configuration in ServiceNow. In the console, navigate to System LDAP > Create new Server
Provide the details of your LDAP environment and press Test Connection at the bottom to make sure it’s working properly:
Lastly, we’ll have to enable scheduled loads and execute them once to import our users and groups. In the console under System LDAP > Scheduled Loads, select your Groups Import section. Select Enable and select Update to save the setting. Then press Execute Now.
Repeat the process for the Users Import:
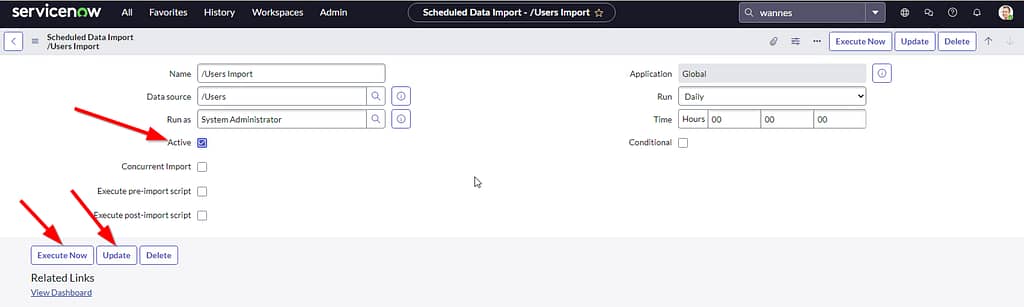
Verify your users where successfully imported under System Security > Users & groups > Users.
Install ServiceNow Provisioner files on PingFederate
PingFederate offers an out-of-the-box integration with ServiceNow. You simply have to download the files to your PingFederate server.
The installation of this module is straightforward and requires you to:
- Stop the PingFederate service.
- Extract the zip file and copy the content of the dist directory to your <pf_install>/pingfederate/server/default/deploy directory.
- restart the PingFederate service.
Configure SAML in ServiceNow
To configure the SAML federation with PingFederate, You have to install the “Multiple Provider Single Sign-on Installer” plugin in your instance.
In the ServiceNow console > System Definition > Plugins, search for and install the Multi Provider SSO Installer:
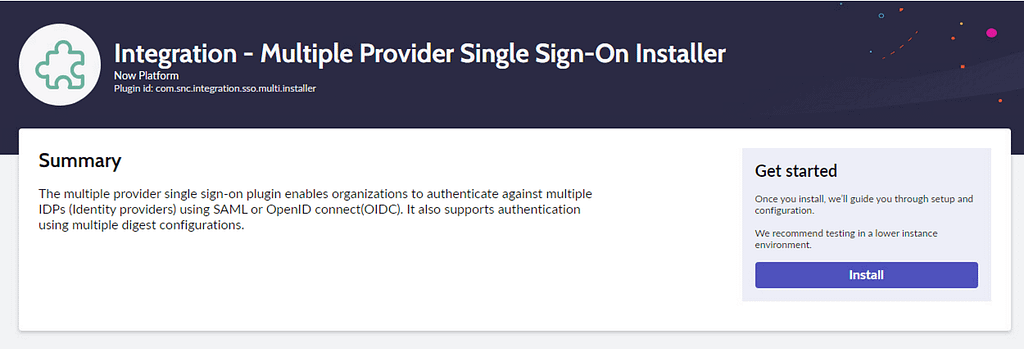
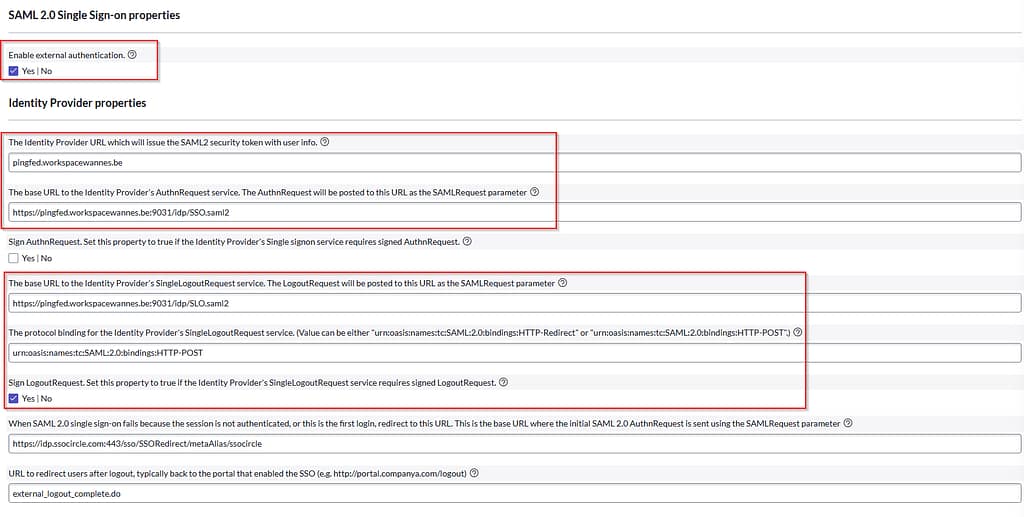
Once the plugin has been installed, navigate to SAML 2.0 Single Sign-On > Properties and provide following input:
Enable external authentication: Yes
Identity Provider properties:
- Identity Provider URL (e.g. pingfed.workspacewannes.be)
- This should match the SAML 2.0 Entity ID configured on PingFederate > System > Server > Protocol Settings!
- Base URL to the IdP’s AuthnRequest service (e.g. https://pingfed.workspacewannes.be:9031/idp/SSO.saml2
- Base URL to the IdP’s SingleLogOutRequest service (e.g. https://pingfed.workspacewannes.be:9031/idp/SLO.saml2
- protocol binding for the Identity Provider’s SIngleLogoutRequest service: urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST
- Sign LogoutRequest: Yes
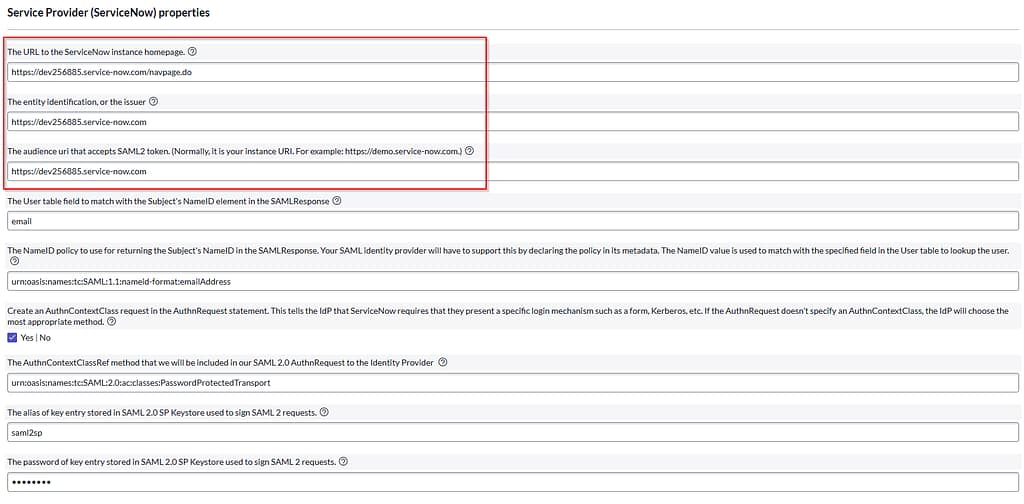
Service Provider (ServiceNow) properties:
- URL to the ServiceNow instance homepage: https://devXXXX.service-now.com/navpage.do
- Issuer: https://devXXXX.service-now.com
- Audience URI: https://devXXXX.service-now.com
- User table field to match: user_name
- NameID policy: urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified
At the bottom of the page there’s a button to enable debug logging, which you’ll need to enable in case of problems with the SAML federation.
Click save.
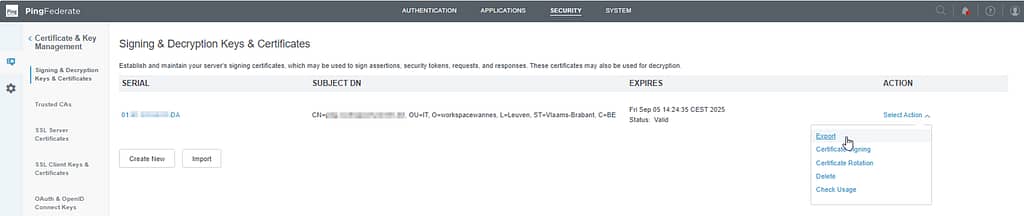
As the next configuration step on the Service Provider side, we have to upload the signing certificate used by PingFederate. To export the signing certificate from PingFederate, navigate to Security > Signing & Decryption Keys & certificates and export the certificate (not including the private key of course):
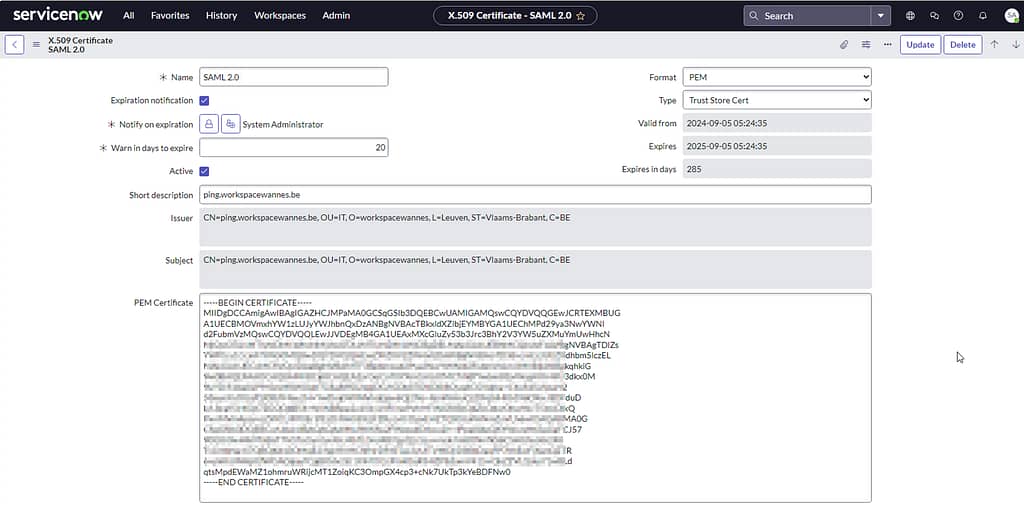
Open the .crt file using a text editor and copy the content.
Back in your ServiceNow instance, navigate to SAML 2 Single Sign-On > Certificate and select New. Give the certificate the name SAML 2.0 and paste the content of the .crt file in the PEM certificate field:
Configure ServiceNow as a service provider in PingFederate
To start the IdP side of the configuration, we first need to export the metadata from ServiceNow. You can find it at SAML 2 Single Sign-On > metadata. Copy the content and save it for the following steps.
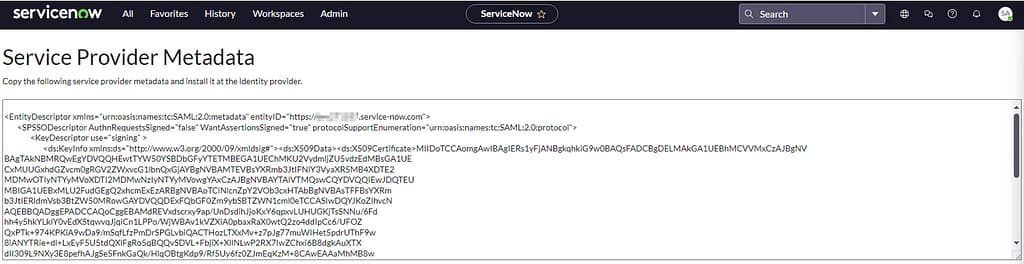
In the PingFederate admin console, navigate tot Applications > SP Connections and select Create Connection. Choose the use a template, select the ServiceNow connector and import the metadata from the previous step.
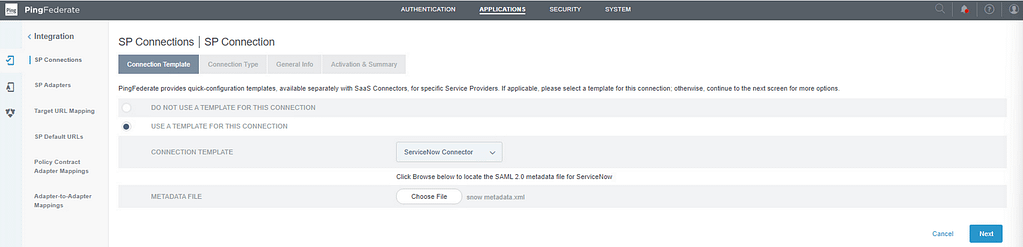
Unselect Outbound Provisioning on the connection type screen:
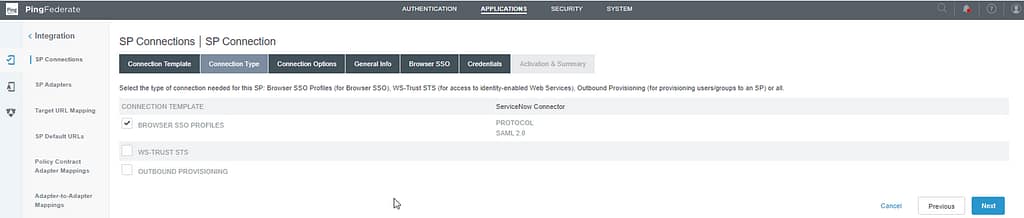
Leave the default Browser SSO setting on the Connection Options screen and click next:
On the General Info screen, you can optionally set a more convenient Connection Name:
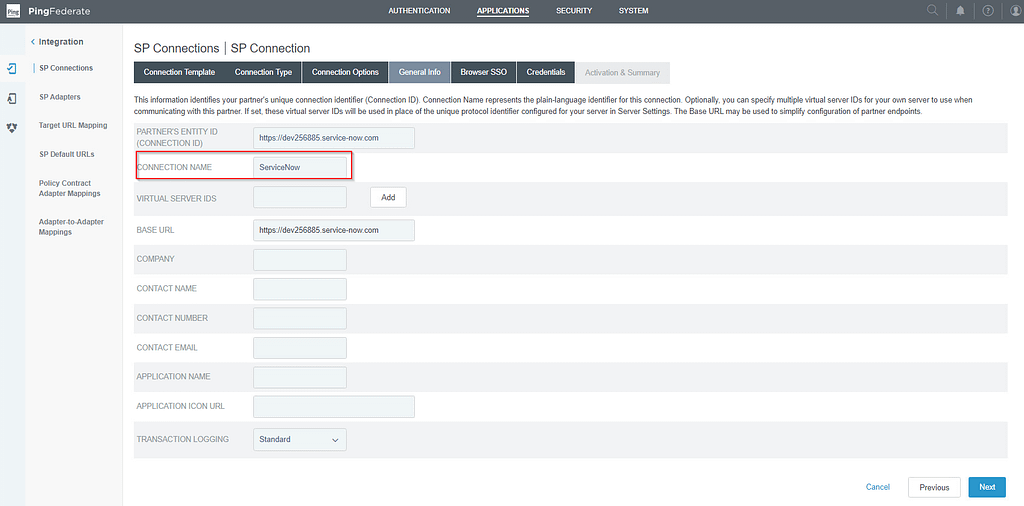
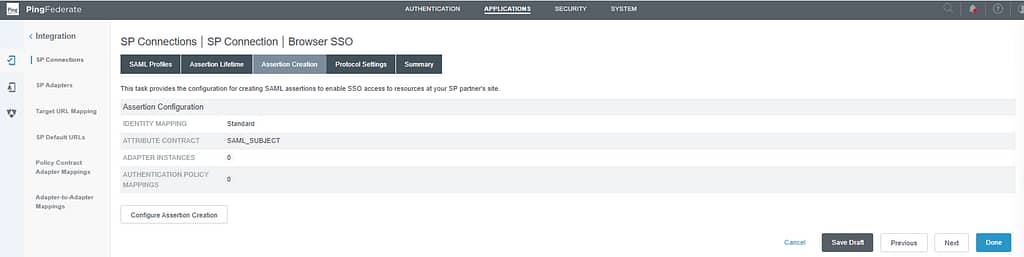
On the Browser SSO screen, click Configure Browser SSO. Click next until you reach the Assertion creation screen. Select Configure Assertion Creation:
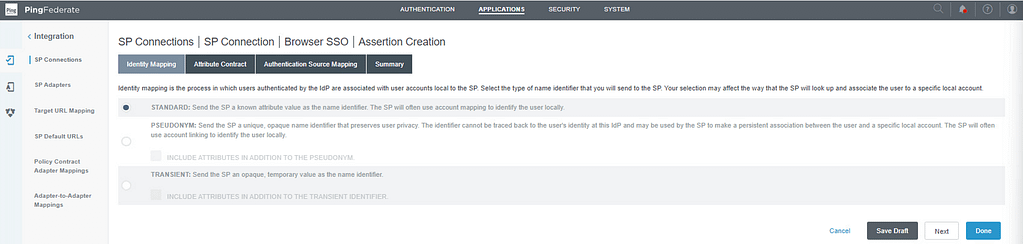
On the Identity Mapping screen, select Standard:
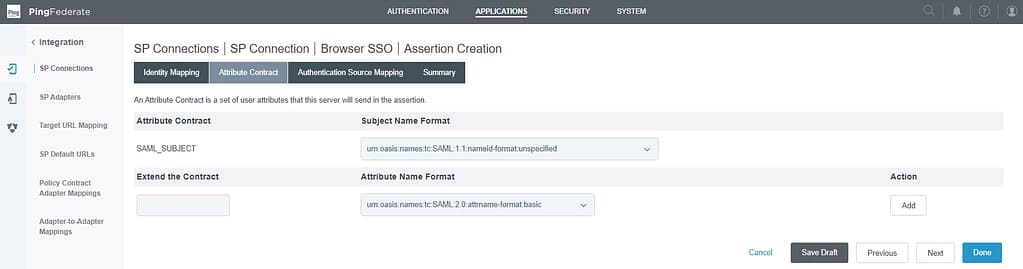
On the attribute contract tab, select unspecified as the Subject Name Format.
On the Authentication source mapping screen, select Map New Adapter instance:
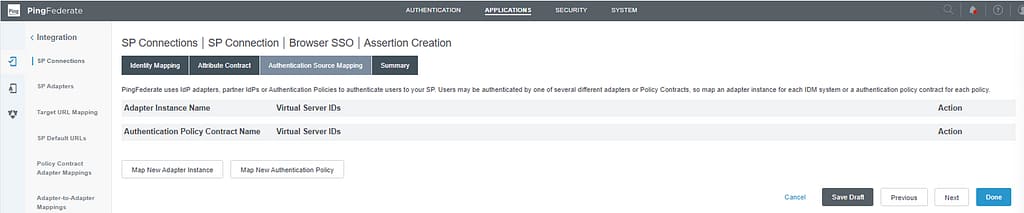
On the Adapter instance screen, select HTML Form AD:
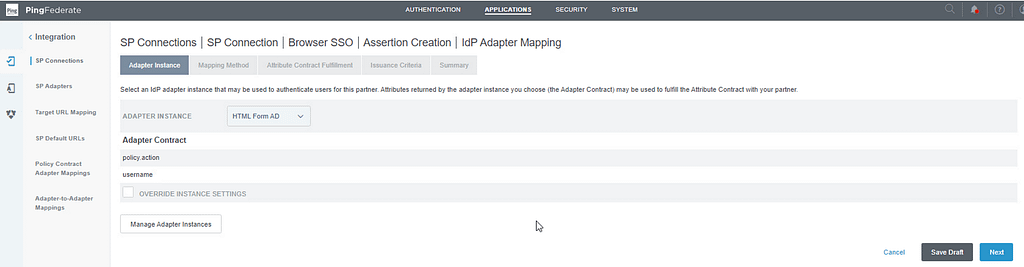
On the Mapping Method screen, select the option to use only the adapter contract values in the SAML assertion:
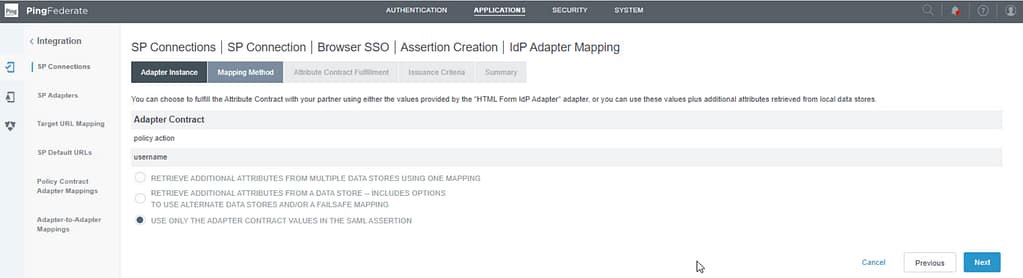
On the Attribute contract fulfillment screen, select Source as Adapter and set the value to username:
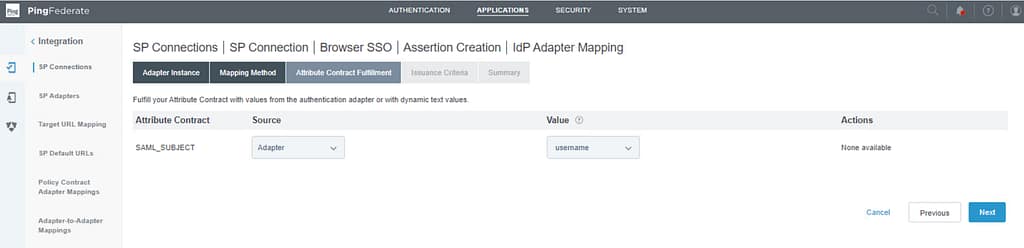
Press next on the Issuance criteria screen. Review the settings on the Summary screen and click Done.
On the Protocol Settings screen, select Configure Protocol Settings:
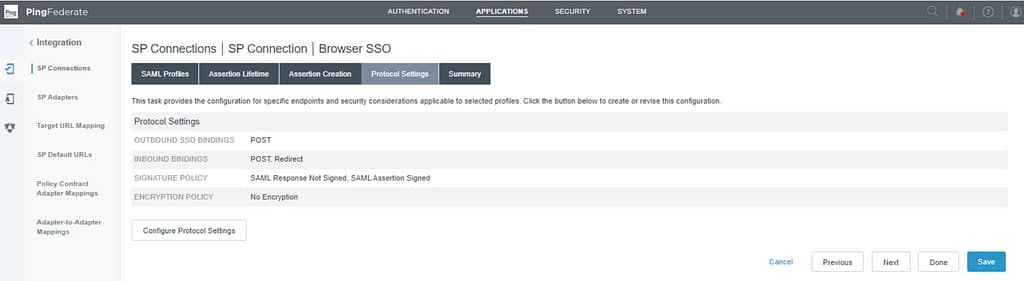
Verify settings on the Assertion Consumer Service URL tab:
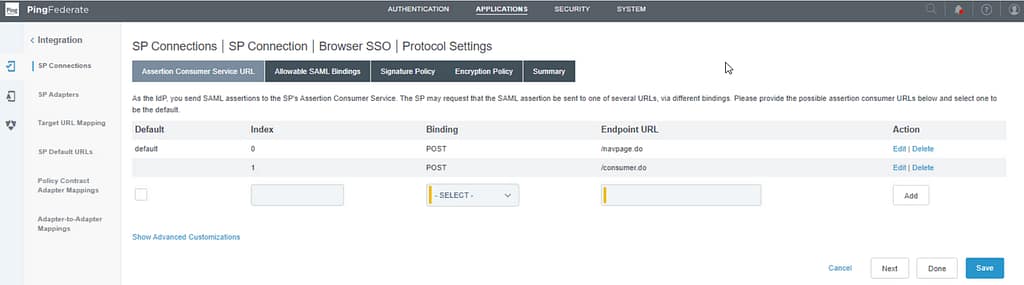
Select Post and Redirect on the Allowable SAML Bindings tab:
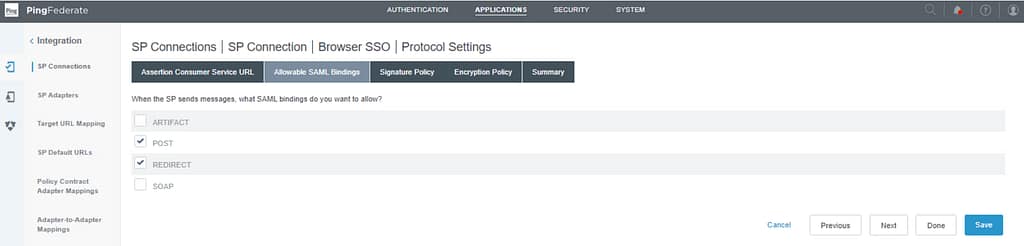
Select Always Sign Assertion on the Signature Policy tab:
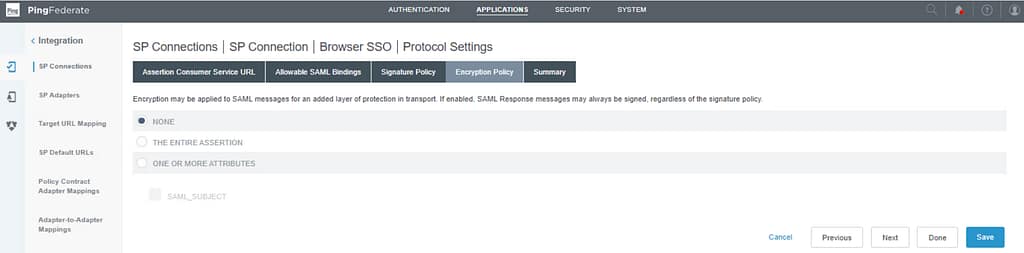
Select none on the Encryption Policy tab:
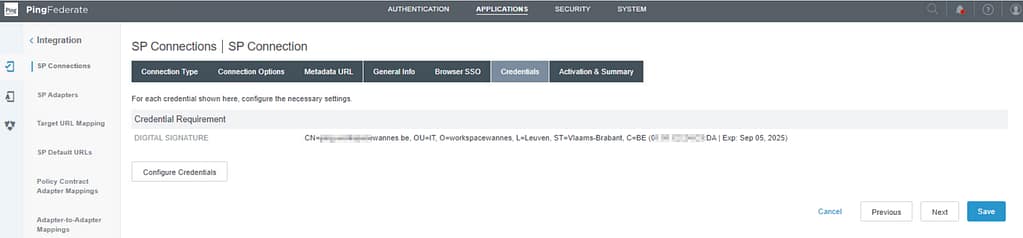
Click Next and Done until you return to the Credentials screen. Select Configure credentials:
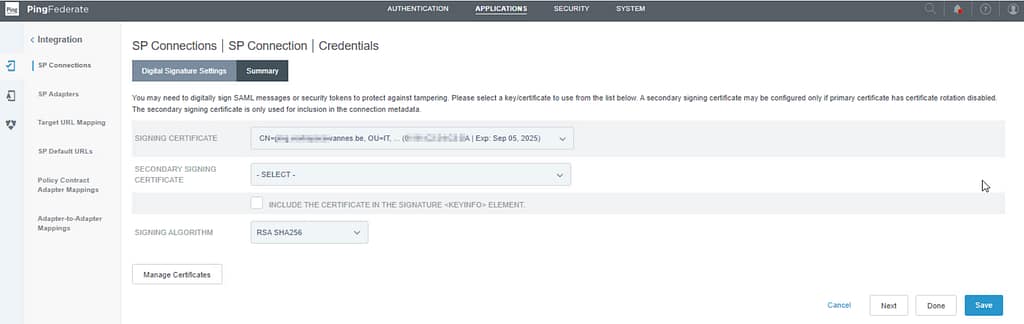
Select your signing certificate and click Done:
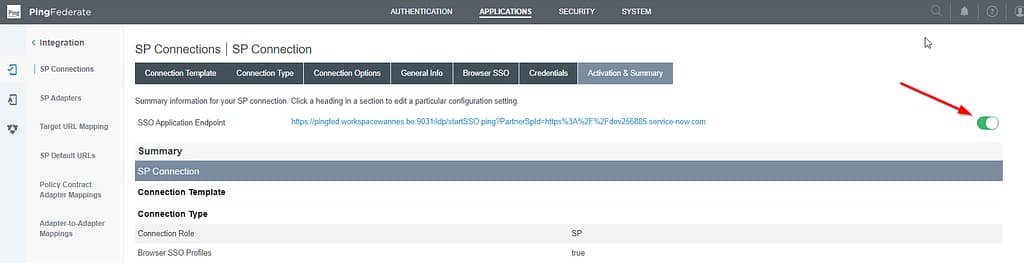
Click next until you reach the Activation & Summary screen. Make sure you activate the service provider Click Save.
In an incognito browser session, navigate to the base URL of your tenant (e.g. https://devXXXXX.service-no.com). You should be redirected to your PingFederate server and see an authentication screen to enter your AD username and password.
In chapter 5 of this tutorial, we will modify this configuration so that authentication requests for the Android platform will be redirected to Workspace ONE Access. But first I will configure an additional service Provider that needs to query LDAP for additional user attributes: Office 365. See you in chapter 4!
Troubleshooting
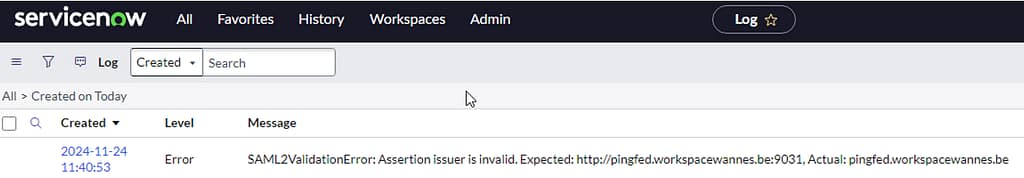
In case of problems, review the ServiceNow debug logs at System Logs > System Log > all. Here’s an example of an error where I had misconfigured my Identity provider URL (actually I had it configured as asked in the Ping documentation):
On the PingFederate side, you can find useful logs at \PingFederate\log (check the audit, transaction and server logs for clues)
