Initial PingFederate Setup
this blog is the second part of the tutorial.
Part 3: ServiceNow integration with PingFederate
Part 4: Office 365 integration with PingFederate
Part 5: PingFederate integration with Workspace ONE Access
Assumptions
- You’ve built a server running an Active Directory domain controller and created some user accounts for testing
- You’ve created a second server for PingFederate and joined it to the domain
- You’ve created both an internal and a public DNS record for your PingFederate server
- You’ve got a publicly trusted SSL (wildcard) certificate for that domain name
Gathering the required files for installation
Ping offers a trial license for PingFederate, which is valid for a month. If it expires, you can simply request a new trial license and upload that to the server. To gain access to the PingFederate installation files and trial license, you’ll need to create an account here. Just provide your email address and complete the account setup process.
Once you’ve completed that first part, log on to the support portal and navigate to your account. You should find a “Manage license keys” button there:
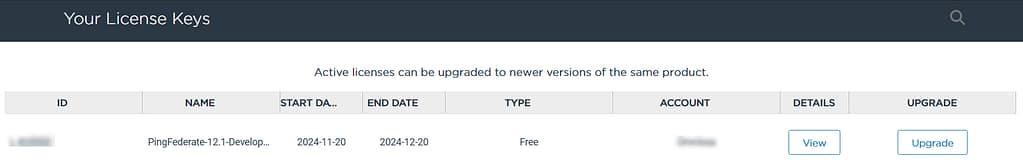
On this page, you can request your PingFederate license key:

If you then click the Next button, you can download (and renew) your license file to your PingFederate server:
You’ll also need the PingFederate Installer, which can be found here: https://www.pingidentity.com/en/resources/downloads/pingfederate.html
Copy the MSI installer, license file and publicly trusted certificate to your PingFederate server.
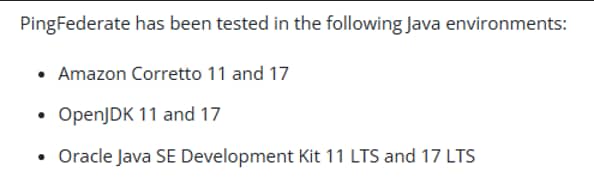
Lastly, the PingFederate server requires Java to be installed and the JAVA_HOME environment variable to be set on the machine. Supported versions and configuration steps can be found here: https://docs.pingidentity.com/pingfederate/latest/installing_and_uninstalling_pingfederate/pf_install_java.html

Initial PingFederate Setup
Now that we have everything in place, it’s time to launch the installation MSI.
For the purpose of this lab setup, I’m using a Standalone server:

I’m using the default admin port (9999) and HTTPS port (9031). The installer doesn’t open the firewall ports for you, so you’ll need to open port 9031 for incoming traffic manually if you want this server to respond to any authentication requests.
Once the application installed successfully, you can access the admin portal on https://localhost:9999 and accept the Terms and Conditions.
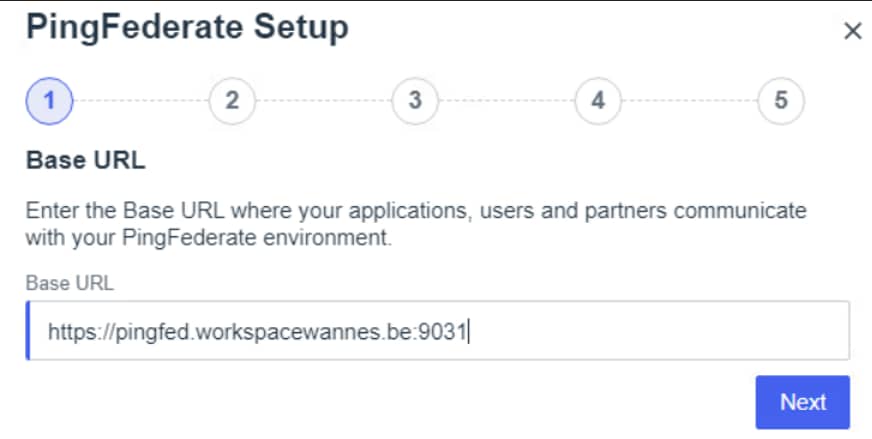
Next, you’ll be asked to provide the FQDN:
You can connect to a PingOne tenant (I skipped that part):
Upload the license file you obtained in one of the previous steps:
Provide a default admin password:
Once these steps have been completed, we can configure certificates. In the console, navigate to Security > Certificate & Key Management > Signing & Decryption Keys. For the sake of this lab, I decided to generate a self-signed certificate:
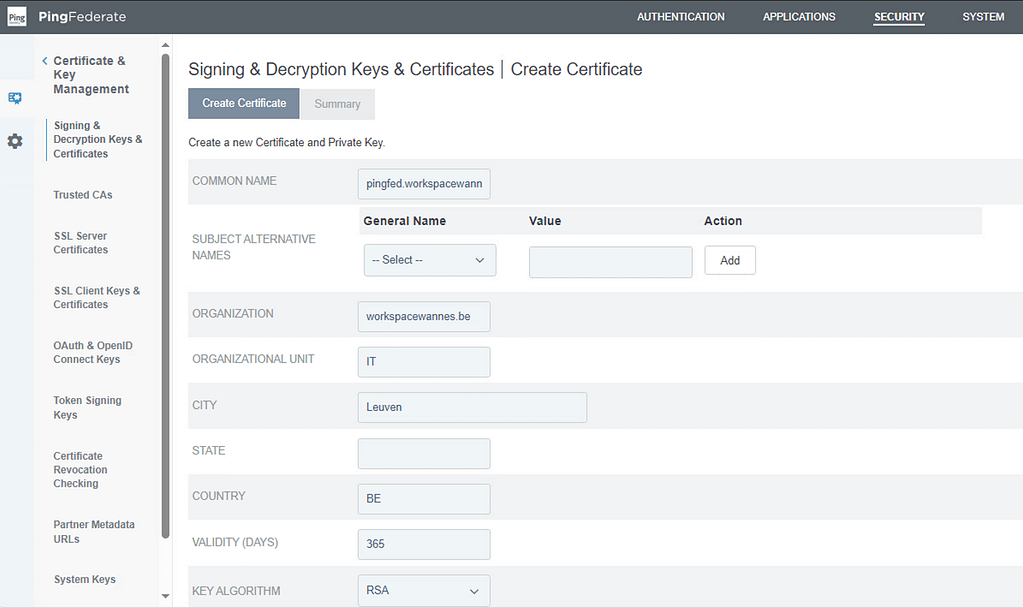
Next, you’ll have to install a server certificate. Certain SaaS apps like Office 365 demand this is a publicly trusted certificate, so I used my lab’s wildcard certificate.
Navigate to Security > Certificate & Key Management > SSL Server certificates and import your certificate. Once uploaded, make sure to activate the certificate for the Runtime server (and optionally Admin console)
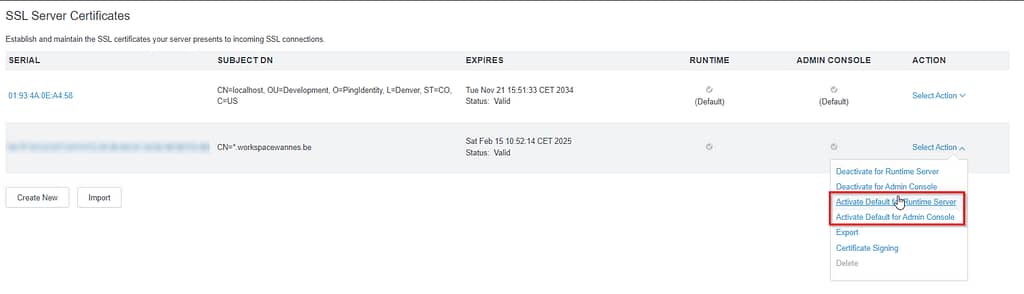
Deactivate the default pre-installed self-signed certificate and restart the PingFederate service to complete this step.
Active Directory Integration
If we want our users to be able to authenticate to PingFederate using their AD credentials, we have to connect both platforms. This involves the three steps listed below.
- Configure an LDAP Data Store: “Datastores represent external systems where user attributes and other data are stored. Once defined, you can configure PingFederate to retrieve user attributes from datastores for contract fulfillment and token authorization in various use cases.”
- Configure an LDAP Username Password Credential Validator (PCV): “Validates credentials based on an LDAP look-up in an organization’s Active Directory”
- Configure an HTML Form Adapter: “PingFederate packages an HTML Form Adapter that delegates user authentication to a PCV, such as an LDAP Username PCV. The adapter validates credentials against a user repository through a PCV instance.” (it’s basically a web page you can tweak that displays a sign-on page if no valid authentication token is found, at least that’s how I translated it)
Configure a Data Store
First, we’ll need to create a user object in AD that will be used by PingFederate to query your Active Directory, much like you already have such an account for your AirWatch Cloud Connector or Workspace ONE Access LDAP integration.
To configure the Data Store, navigate to System > Data & Credential Stores > Data Stores and select Add New Data Store
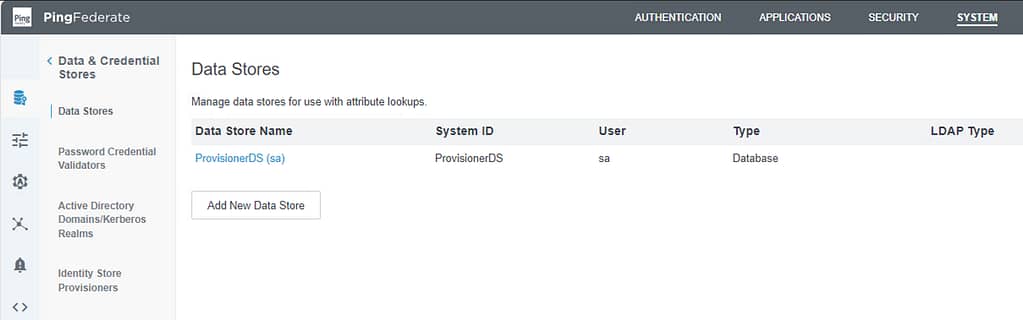
On the Data Store Types screen, provide a name and set the Type to Directory (LDAP):
On the LDAP Configuration screen, provide the proper configuration for your environment. For my lab environment, it looks like this:
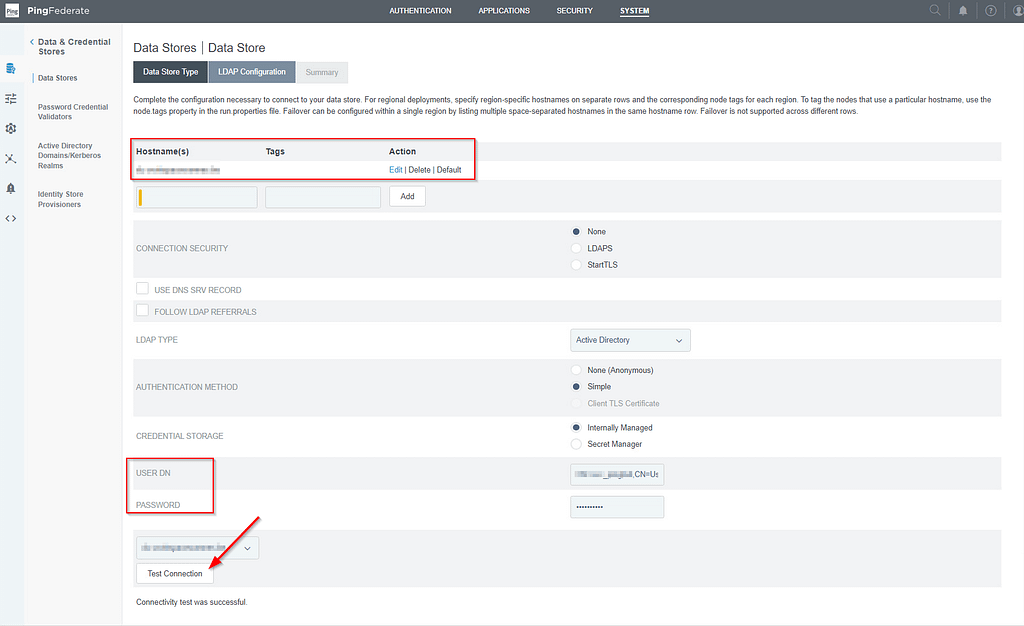
Use the Test Connection button to confirm your configuration is working. Click Next and on the Summary screen, click Save.
Configure the Password Credential Validator
To configure the PCV, navigate to System > Data & Credential Stores > Password Credential Validators and select Create New Instance:
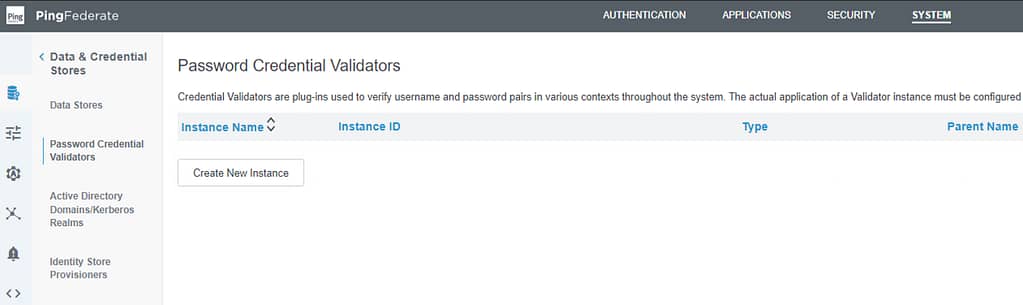
On the Type screen, provide an Instance Name and ID and select the type LDAP Username Password Credential Validator:
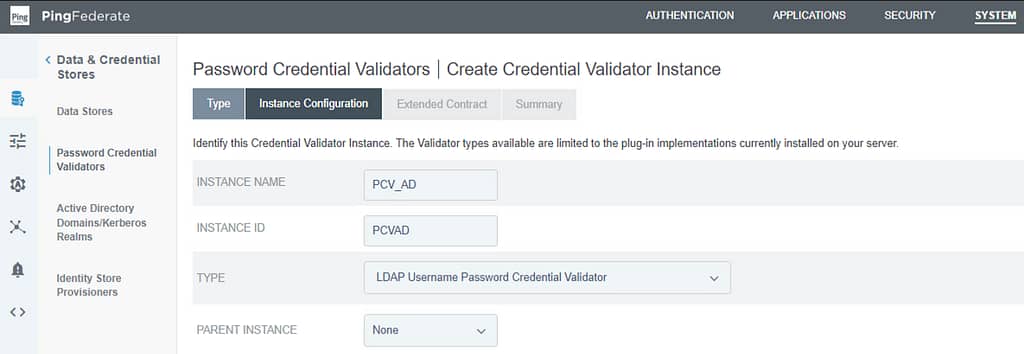
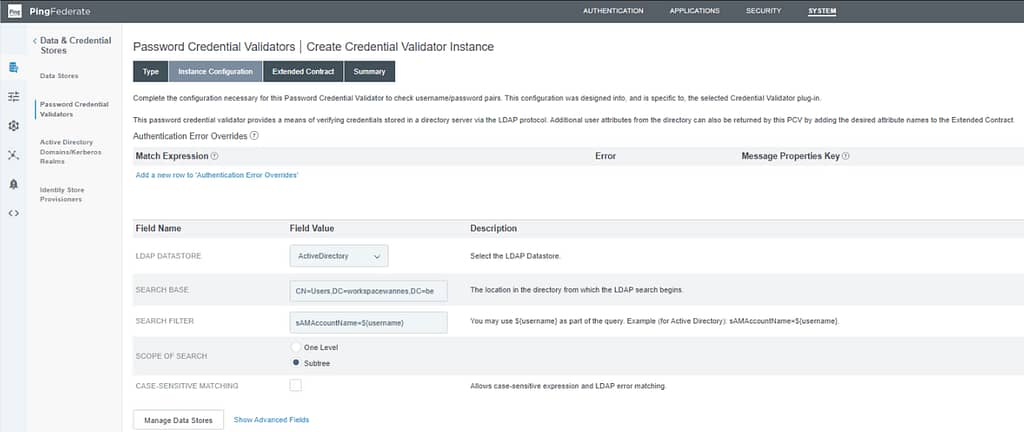
On the Instance Configuration screen, select your LDAP Datastore created in the previous step, provide the Search Base and filter. For my lab environment, this looks as follows:
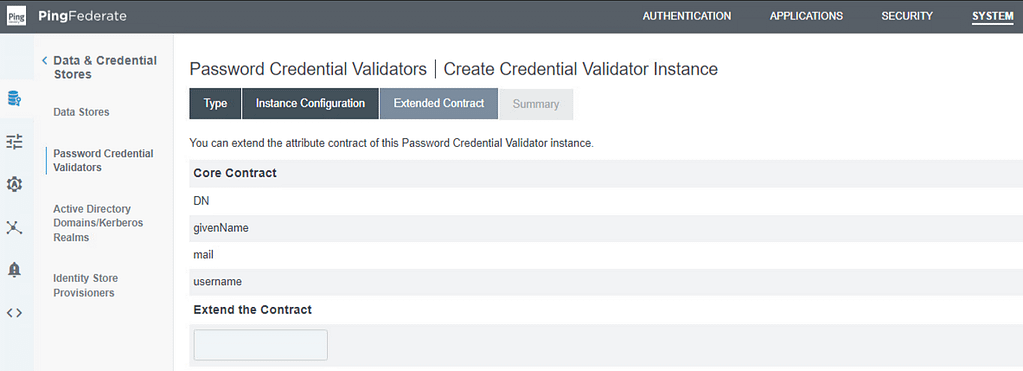
I didn’t make any changes in the Policy Contract screen, so select next and on the Summary screen click Save.
Configure the HTML Form Adapter
As the last step in this procedure, we’ll configure the HTML form Adapter. Navigate to Authentication > Integration > IdP Adapters and click Create New Instance:
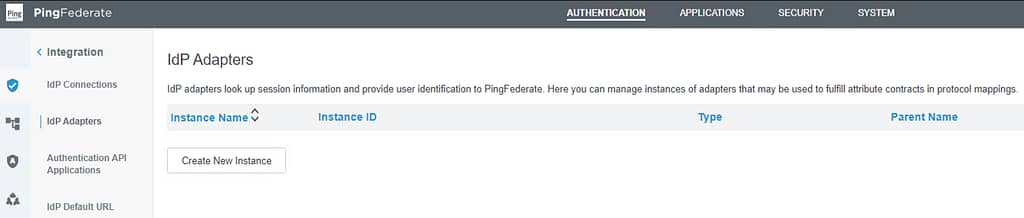
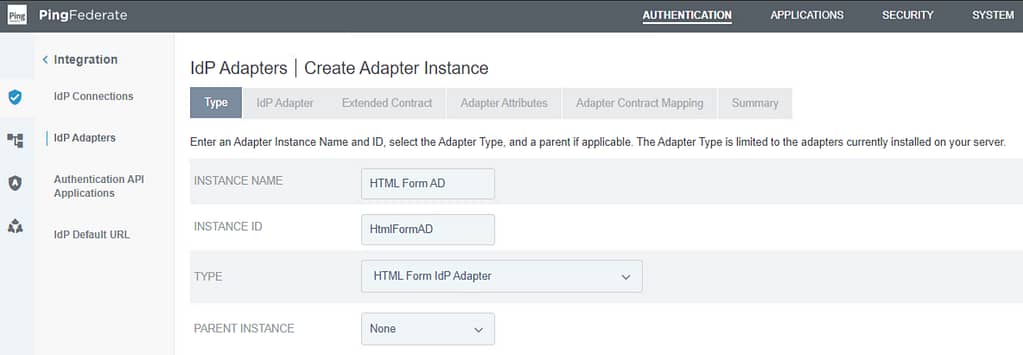
On the Type screen, provide an Instance Name and ID. Set the Type to HTML Form IdP Adapter:
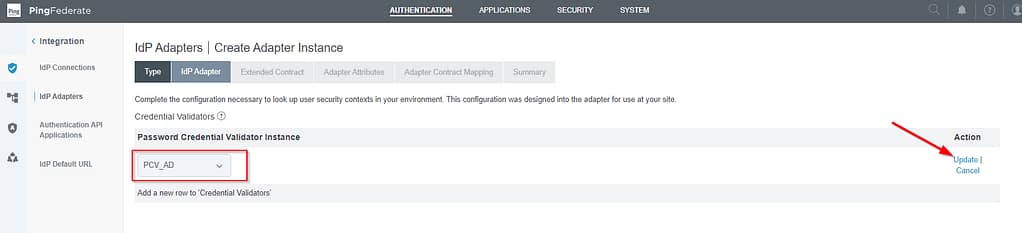
On the IdP Adapter screen, you have to link the PCV created in the previous step:
I didn’t modify any of the other settings in my lab. But if you want to make changes to the looks and feel of your authentication screen, you can (make a copy of and) edit the default template, which is located at <pf_home/server/default/conf/template/html.form.login.template.html). If you made a copy, select the new file in the Login Template field.
On the Extended Contract screen, click Next.
On the Adapter Attributes screen, select the Pseudonym option for username and click next:
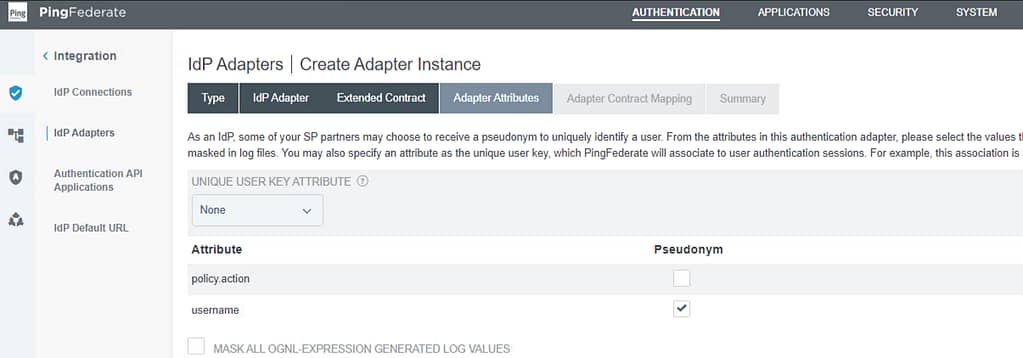
On the Adapter Attributes & Adapter Contract Mapping screens, click Next.
Review your configuration on the Summary screen and click Save.
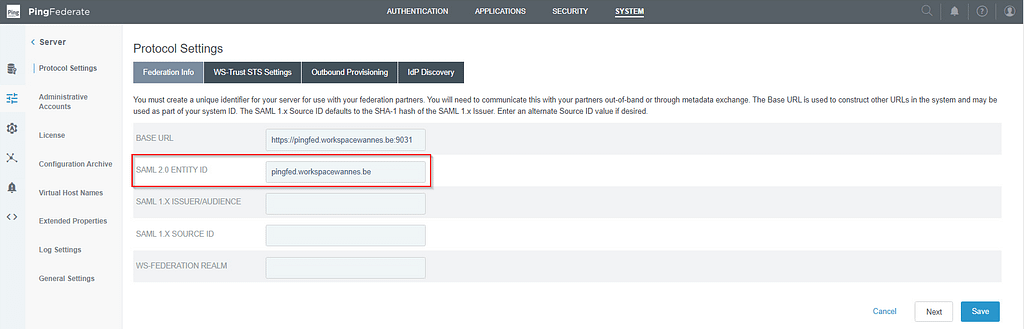
Configure SAML 2.0 Entity ID
in the PingFederate admin console, navigate to System > Server > Protocol Settings and enter a SAML 2.0 Entity ID value:
Conclusion
This concludes the basic setup of PingFederate and this part of the blog series. In the following post, we’ll add our first Service Provider (ServiceNow) and test the sign-on process using the AD integration we just configured.